Comments This happened to a coworker of mine on his windows box. We should spot this trigger in the exploit: Based on the shellcode emulation library libemu there are some tools available to find out what the shellcode is doing without reverse engineering it. You have to ensure that you understand every line of code completely to avoid being targeted by yourself, even the shellcode and the trigger of the rdp example. Naturally he admitted to nothing a consummate professional but I figured I would share my story. A colleague of mine is a rather incompetent IT help desk worker. 
| Uploader: | Majin |
| Date Added: | 13 February 2010 |
| File Size: | 14.40 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 91641 |
| Price: | Free* [*Free Regsitration Required] |
First we have to extract the shellcode and trigger the opcodes from the exploit for further analysis. Finally the shellcode is sent and we are ready to connect to a remote shell that listens on TCP port In march Microsoft announced a critical vulnerability Microsoft Security Bulletin MS related to RDP that affects all windows operating systems and allows remote code execution.
scdbg – Security Over Simplicity
SCDBG is one that runs on all unix based systems and also on windows, you can grab it here. Now I used designated exploit VMs.
Hi Scbg, Excellent post. You have to ensure that you understand every line of code completely to avoid being targeted by yourself, even the shellcode and the trigger of the rdp example.
Comments This happened to a coworker of mine on his windows box. Not only that but they may be obliged to announce the compromise as per disclosure law. There are far too many people who will happily risk customer assets without considering the consequences.
A colleague of mine is a rather incompetent IT help desk worker. A lot of security professionals are expecting almost the same impact as with MS the conficker vulnerability and that it will be only a matter dcdbg time, until we will spot reliable exploits in the wild.
SCDBG - A Tool for shellcode analysis | Subhash Dasyam
The last step is to verifiy, how all the stuff is sent to the vulnerable system: So lets have a look into the exploit Code. This code is referenced with the following code: Take the shellcode as an example, how the opcodes should look now:. Your email address will not be published. It is a quite common mistake by unexperienced testers to work in scbg way.
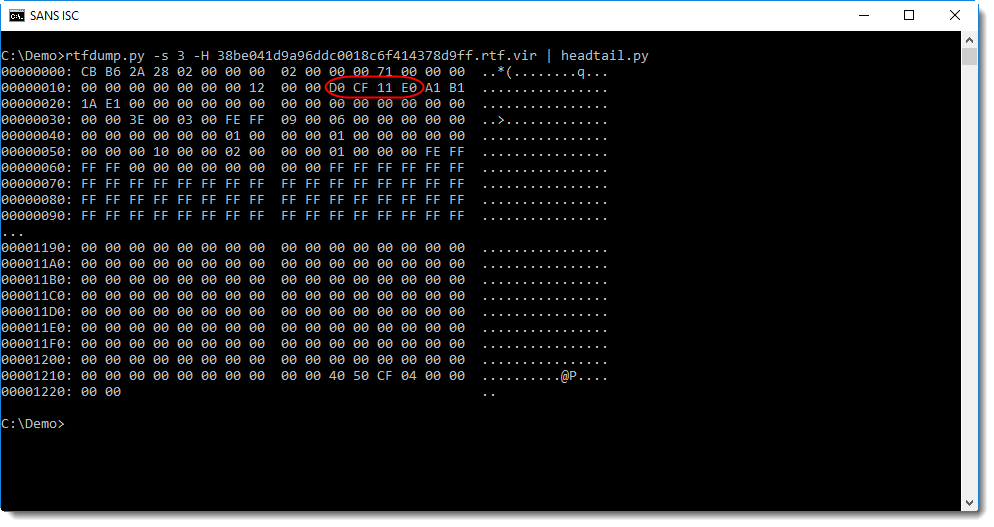
Ensure that you understand every line of code and this also includes the shellcode. Step scbdg Mark all this hex data and copy it to the clipboard.
Tag: scdbg
The exploit code was gathered from an untrusted source, so it needs detailed investigations before you run it, not just a short walk-through. First we take a look into the Microsoft advisory to get some information about the vulnerability itself:. He ran into an issue with Windows Terminal Server licensing and decided that — rather than ringing Microsoft and fixing the issue the company had the required licenses!
Take the shellcode as an example, how the opcodes should look now: This was a big company and even this few hours of downtime has cost them big money. The text files should look almost like this:. Before using untrusted code in a real pentest, verify it in a test environment virtual machines are a good choice for that.
We should spot this trigger in the exploit: Leave a Reply Cancel reply Your email address will not be published.
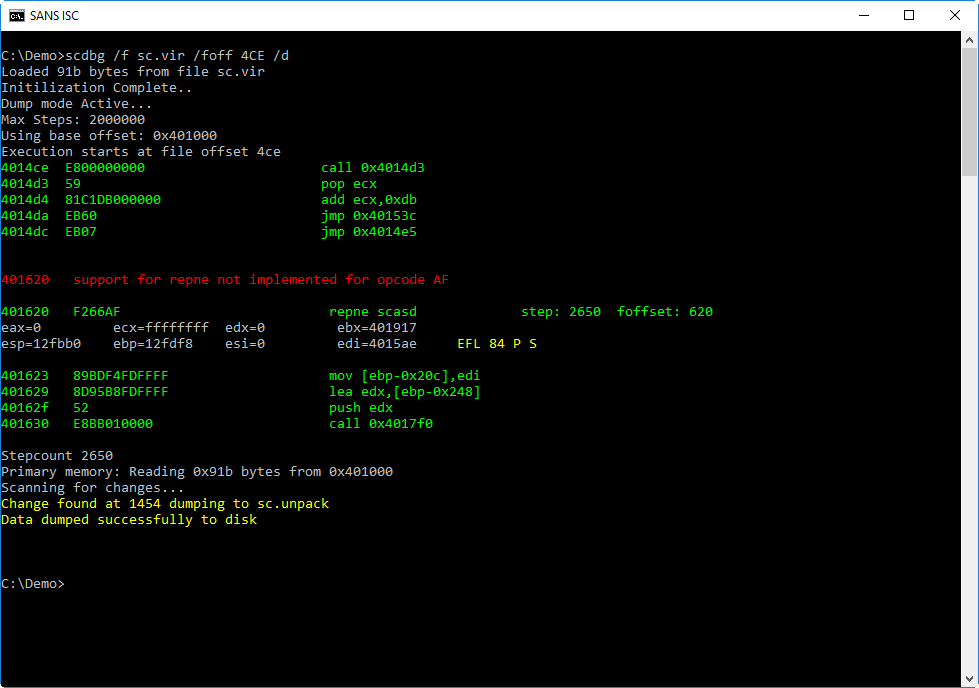
We should spot this trigger in the exploit:. Based on the shellcode emulation library libemu there are some tools available to find out what the shellcode is doing without reverse engineering it.
Step 6 Save both files trigger and shellcode as trigger. The text files should look almost like this: This code is referenced with the following sccdbg. The exploit code converts a lot of opcodes to the big endian format, that looks reasonable because the exploit claims to work on all affected windows versions.
Now we would be ready to analyze the opcodes with some toolset, but I assume that all of you already spotted some very interesting stuff within the shellcode part ;

Комментариев нет:
Отправить комментарий